Kubernetes, also known as K8, is an open-source framework that automates the deployment, scaling, and management of containerized applications.
Governance of Kubernetes may not sound interesting, but it is very important if you want to create an enterprise containerized application.
What is Kubernetes Governance?
While working with Kubernetes, to standardize the services, we must ensure that all groups or teams performing the deployment follow certain rules, policies, and processes defined within the organizations. Even if we are working with a small number of clusters, we must keep all the clusters in sync. Without governance and automation, it becomes very tedious to manage workloads on Kubernetes.
In order to tackle this scenario, governing the Kubernetes cluster is mandatory. With governance, DevOps teams must be able to verify and enforce rules across the enterprise organization. There are multiple dimensions to governing Kubernetes clusters.
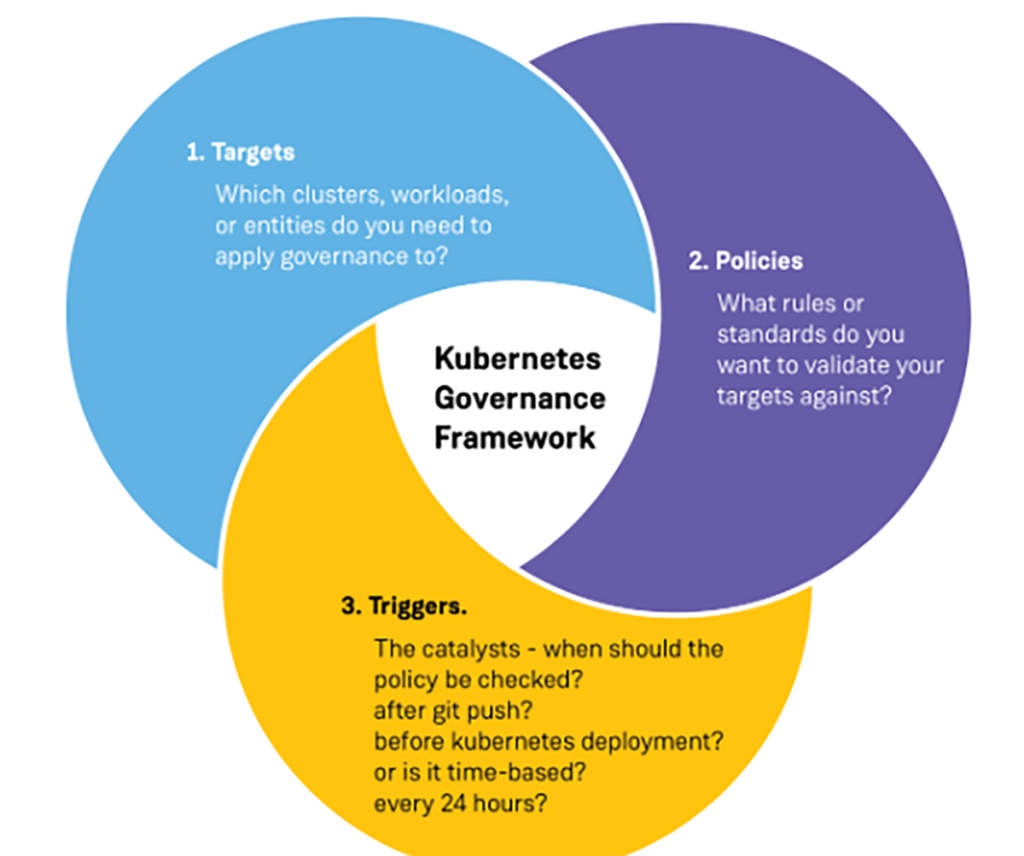
Targets
Clusters or workloads of the Kubernetes cluster where we want to apply governance.
Policies
Policies defy the rules we want to validate against the defined targets.
Triggers
It determines what time the policy should be checked: after the git push, before the Kubernetes deployment, every 24 hours, etc.
Once the target and policies are defined, we have to enforce those policies on the target system to ensure compliance. Following these processes manually is very difficult for the enterprise organisation. Best way to enforce these policies is to automate the compliance process based on the triggers defined so that defined policies can be managed on their targets.
Forms of Governance
Let’s understand why use Kubernetes governance using the policies in detail. We can define and perform governance of Kubernetes in multiple dimensions to control authorized users who should be able to access the cluster and limit the usage from the infra point of view.
Access Control
Access control involves enabling and enforcing role-based access control for kubernetes clusters. For example, disable the default namespace to force every object in the cluster to be assigned to a proper namespace.
Using kubernetes admission controller, we can intercept requests to the Kubernetes API server to the persistence of the object after the request is authenticated and authorized. The controllers are compiled into the kube-apiserver binary and it is configured by the administrators.
There are two special controllers: MutatingAdmissionWebhook and ValidatingAdmissionWebhook. Admission controllers limit requests for creating, deleting and modifying objects to proxy. This admission controller process proceeds in two phases. During the first phase, mutating admission controllers are running. Then in the second phase, validating admission controllers run. If any of the requests is rejected in any phase of the controller, then the error will be returned to the end users.
Admission controller is required for many advanced features of the Kubernetes cluster. So, the Kubernetes API server that is not correctly configured with the right set of admission controllers is an incomplete server and it might not support many features.
If you want to turn on the admission controller then the following command line is used. So, depending on the way the Kubernetes cluster is deployed and how the API server is started, we need to apply the admission controller settings in a different way.
kube-apiserver –enable-admission-plugins=NamespaceLifecycle,LimitRanger …
Reliability
In order to ensure and improve the continuity of our business application, we have to make sure that the system is highly available and reliable. We can do this by verifying that the replica count is 2 or more to increase the availability of the application, or ensuring that the readinessProbe and livenessProbe are defined in the container.
Image Management
Companies or organizations can specify which container images should be used for which cluster or conditions to be fulfilled before using the container image for the production workload.
Networking
With networking, we can determine which pods or containers should be able to interconnect each other. Common governance rules including the cluster topology and general cluster configuration constraints should be defined at an enterprise level.
Configurations Constraints Policy
With the configuration constraints and policies, we can define the resource configurability rights as well as the resource access and limits. Consider an example where the business unit A is allowed to create clusters in Azure and AWS and use the resources upto a certain limit. Various policies regarding configurations and constraints of the clusters can be automated to minimize the risk for security.
Limit Use Access
With respect to the security policies for the kubernetes cluster, it is very important to limit access to the end users for pods in the cluster. End users of the cluster must be able to access based on the predefined access mechanism and privileges. In such policies, we can make sure that the containers have read-only access to the file system and make sure that allow Privilege Escalation=false in the policy.
Access Administration and Management
To configure RBAC policies, admins need to make sure to provide and limit access to the clusters in a granular manner and use on a per need basis. Administrators can configure Role, ClusterRole, RoleBinding, and ClusterRoleBinding, which helps define access to the cluster resources in detail.
Conclusion
As many enterprise organizations are focusing on building containerized applications considering its advantages, major focus on topics such as security, governance, compliance, and operations of Kubernetes cluster is required. There are various tools like K9s, Kontena Lens, WKSctl, cAdvisor, and Weave Scope that can help overcome the basic challenges involved in managing and governing Kubernetes multi-clusters.